We entrust our information to third-party services that do everything in their power to protect it from cyber-attacks. While this is very convenient, the truth is that we only have their word and a combination of legal, administrative, and technical safeguards.
But lately, our trust in third party custodians to keep our information has been slowly declining, as was the case with the people who woke up one day to find out that their Cyprus bank accounts have been raided by another country’s government or the Canadian truckers who lost their rights to transact.
In this article, we will dive deeper into the reasons behind these security issues and offer ways that users can ensure private key encryption.
Why is data ownership an issue?
The main advantage of decentralized technology is that we have the ownership of our information. Yet this is also its biggest weakness and one of the reasons why decentralized networks did not gain that much traction.
We heard a lot of stories about people losing value kept on decentralized networks, like the guy who threw out his hard drive to later rummage through a garbage dump to recover a fortune in bitcoins, or a developer who forgot his password for his crypto wallet and had only two more chances to type in the right password before it’s lost forever.
Another interesting case is the attack that happened in 2016, when a hacker made away with more than 119,000 bitcoin, where, consequently, Bitfinex allocated losses of more than 30% to all customer accounts. There are many victims who still have not reclaimed their assets which, in the meantime, have surged in value.
In essence, when creating a wallet, you are assigned a stream of random numbers that are used in the algorithms for transaction signing and proving ownership. This unique stream of numbers is called a private key and is used in private-public key encryption. Only this number can identify the user on the decentralized network and authenticate actions on it. The likelihood of someone else generating the same number is infinitesimally small. You guessed it right — when this key is lost, there is no one who can authenticate with the network to unlock the value attached to that key.
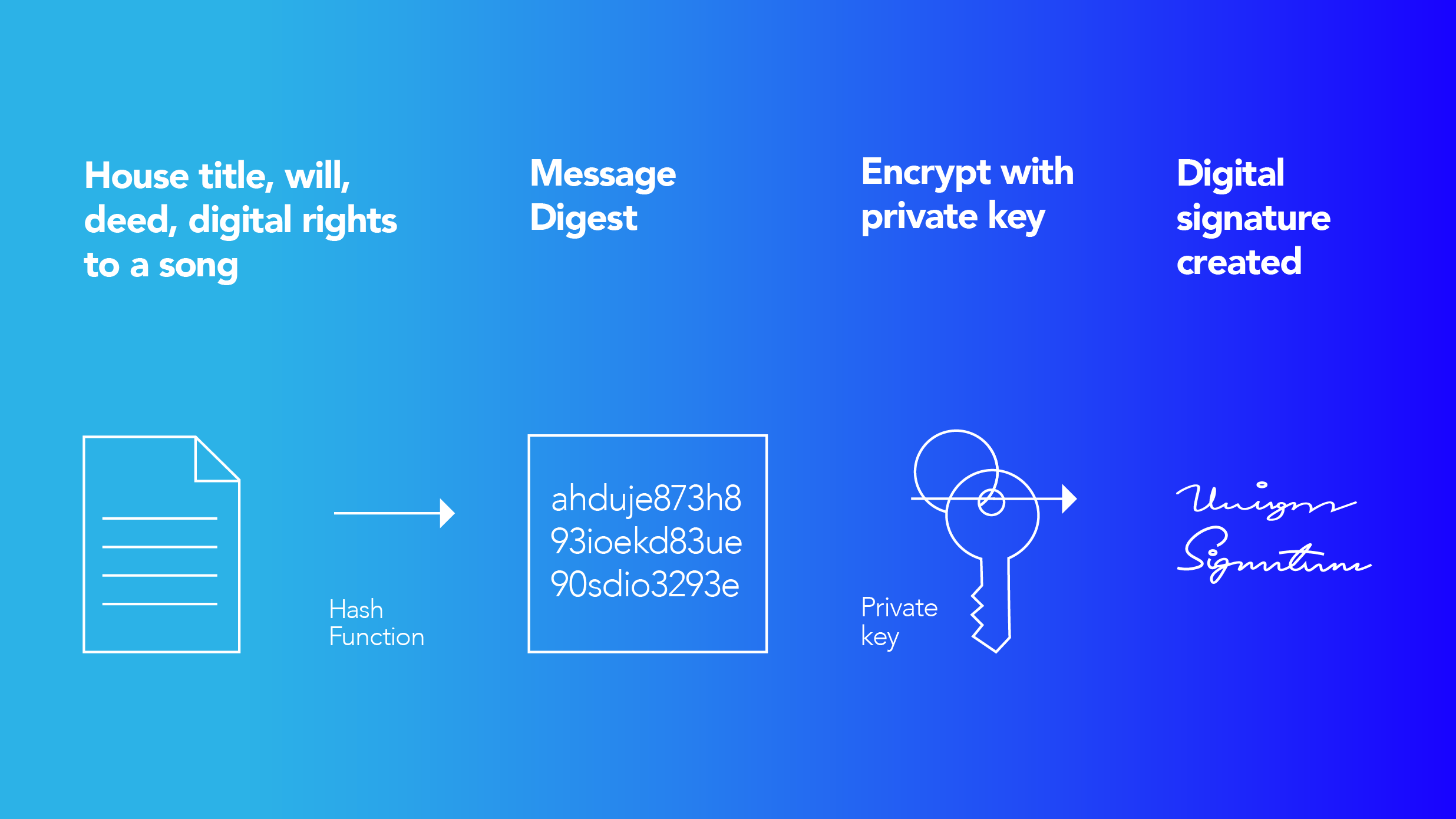
* Hash Function is a mathematical algorithm that maps data of an arbitrary size (often called the “message”) to a bit array of a fixed size (the “hash value,” “hash,” or “message digest”)
There are a few ways the misplacement or the loss of this key (which then locks the value into the blockchain) can be minimized. However, we need to keep in mind that the ability to fully secure digital wallets is mission-critical. Here is a rundown of the types of digital wallets:
Custodial wallets
The easiest way to keep your assets is to entrust private key encryption to a third party (custodian) who will keep them, lowering the chances of its loss. This, however, diminishes the purpose and the value of decentralized networks, where the user has the ownership over their data. In other words, malicious entities can gain access to the third-party service. It becomes a more enticing target as the number of users grows or the third-party service might go rogue.
Non-custodial wallets
Non-custodial wallet allows users to keep the private key in one place only they can access. It can be additionally protected with a PIN or passphrase. They provide private key encryption and utility when interacting with blockchains. A wallet can work with multiple blockchains simultaneously including Ethereum and Alt. Coins, Bitcoin, Solana, and more, all on the same device.
Non-custodial wallets can be:
- Software solutions
- Complete hardware solutions (where the key never leaves the device)
The hardware solution has the highest private key encryption, after paper wallets. Should a thief take possession of your hardware wallet, it is nearly impossible for them to extract your keys. The keys are never exposed to the host machine and therefore to the internet, so they cannot be stolen.
Users can also create their own hardware wallet by air-gaping a device from the network and using another device to interact with the network, while communication between the two uses QR codes.
While hardware wallets are an effective method, it might be a bit cumbersome because users always need two devices to interact with the network. Imagine making personal interactions through the devices to send your friend an NFT or pay for a coffee.
On the other hand, software solutions are easier to use. But the private key is on a device that is connected to the internet, and therefore can be more easily compromised.

* Example of a hardware wallet, where the key never leaves the device — Ledger Nano S
How to back up private keys
Many of non-custodial solutions provide the user with a mnemonic phrase consisting of 12 or 24 words (usually in English), depending on the private key encryption preferences of the user. These words are shown and verified to the user at the time the wallet is created.
The same private key can be recreated using these words by going through an algorithm — it essentially works as a backup phrase. The safekeeping of these backup phrases is trusted upon the user, which means that if access to the wallet and the phrases are lost at the same time, the valuables also get lost.
Key loss recovery solutions
I do not recommend keeping a digital copy of this mnemonic on a device or on the cloud, as this allows malicious users to gain access to it more easily than to the physical copy of it.
The most effective and safe solution is to write it down. There are services that can engrave it in something more permanent, but the most common solution is the paper. The mnemonic phrase can be made safer by keeping multiple copies and can also be split up and stored in many places.
The key can also be split up into multiple parts and each part sent to a different cloud service, from where it can be recovered and merged to get the private key. This, though, requires a setup to keep the order of the parts as well as access to all used cloud solutions.
Distributed backup solutions
Multi-signature technology is another way of keeping valuables more resilient to cyber-attacks or loss. These are advanced algorithms allowing multiple keys to authenticate operations for the same data, which adds another layer of security and backup. Crypto exchanges, brokers/OTCs, investment funds, and other crypto companies use multi-signature technology to secure their cold storage funds.
For example, a company can have multiple keys needed to sign transactions.
- Small value transaction can be signed by any accountant
- Larger value transactions can be signed with both an accountant’s and a supervisor’s key
- Big company investments that involve a board of directors where four of the 12 members need to approve the transaction
There are many more combinations allowing for high customization of private key encryption and backup. So, people can sleep better knowing their digital values are safe.
Private key encryption made simple
One of our clients wanted to make the entire process even safer by giving users access to a hardware wallet without having to work with the mnemonic phrase.
The client came up with the idea of offering users two separate cards—hardware wallets—that can generate the same private key inside them without ever exposing it to the outside world. This allows users to use one card when they are making transactions, and if that card gets stolen or lost, they can use the other card, which they have placed in a safe or some other secure place.
The client approached us to help them develop an application with a user-friendly interface that could perform a variety of advanced functionalities. We developed a complete iOS companion application that allows users to do transactions on blockchain networks.
The solution supports Bitcoin and Ethereum, and the user can, in CLI, use more granular commands, including working with smart contracts and the EOS network. At its core, it is a modern crypto wallet that uses our clients’ cards to sign transactions. We wanted to develop the most efficient solution that would allow users to manage these two cards.
Ultimately, this software provides users with a backup solution that reduces the effort to keep the key safe, and therefore, keep their assets safe even if their primary card gets stolen or lost.
Private key encryption without compromise
There is no one correct method for private key encryption. The key’s safety depends on the risk tolerance of the person holding it. A good strategy is to have different wallets and combine safety with ease of use, depending on the situation.
As trends of adopting web3 technology (where the basis is the private-public key encryption) are speeding up, organizations will need to focus on implementing simple-to-handle and better solutions, and filling in missing links that will assure them that they have an impenetrable and highly secure infrastructure.
Want to learn more about how HTEC’s technology expertise can transform your business? Explore our Technical Strategy and Software & HiTech capabilities.